Dennis Stapp
Smart Products
With the threat of attacks looming large, cyber security is a growing concern for consumers and businesses alike. Designed to protect the EU market from insecure products, the Cyber Resilience Act (CRA) and the Radio Equipment Directive (RED) now hold vendors more accountable. We can help you incorporate the CRA’s ans RED’s stipulations into your product development and manufacturing processes. Why not capitalize on cyber security to gain the competitive edge?
Connectivity puts a host of new functions at users and operators’ fingertips. It opens up exciting opportunities for vendors to differentiate everything from Internet-enabled consumer products to connect industrial machines. But it also amplifies the risk of cyber attack, which can have serious consequences. Cyber security is certainly a regulatory imperative, but vendors would be well advised to also make it a business priority.

The CRA aims to protect consumers and businesses that use products or software with digital components. It requires vendors to take compulsory security requirements into account at all stages of the value chain. Companies must demonstrate that they factor cyber security into the equation throughout the product development process, manage vulnerabilities during the support period, and report incidents to European authorities. Vendors that fail to comply are denied CE certification and will not be allowed to sell their products in the EU. This goes to prevent high-quality cyber security from becoming a competitive disadvantage. Failure to comply may lead to financial penalties and reputational damage.

The RED Delegated Act for Cyber Security introduces new cyber security requirements for all electrical and electronic devices in industrial and consumer products that transmit or receive radio waves. Manufacturers of such products will be required to demonstrate measures to adequately protect the devices against attacks. Manufacturers of IoT devices such as smart TVs, wearables or networked household appliances are also obliged to ensure the privacy of users and to protect against fraud. If companies do not comply with the RED requirements, they will not receive CE certification and can no longer be sold in the EU.
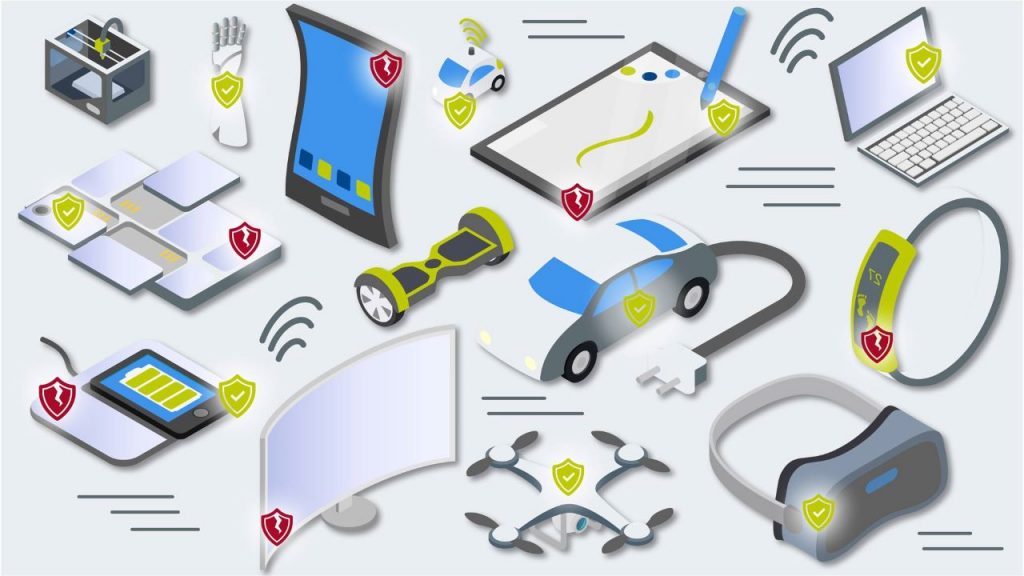
These days, cyber security is a top priority for both consumers and businesses. A successful cyber attack would spell disaster for the trusted relationship between the vendor and customer in both B2C and B2B channels. This is why cyber security is fast becoming a hallmark of quality and a differentiating factor in the marketplace. Companies would do well to consider security at every link of the product development chain.
Count on us to help you incorporate cyber security at every step of the manufacturing process, the software development effort, and the product lifecycle. We can assist you with everything from the cyber security strategy to incident and vulnerability management, and on to product development tasks ranging from risk analysis to testing. If you wish, we can do all this in compliance with the latest cyber security standards such as IEC 62443, NIST Framework, and the like.
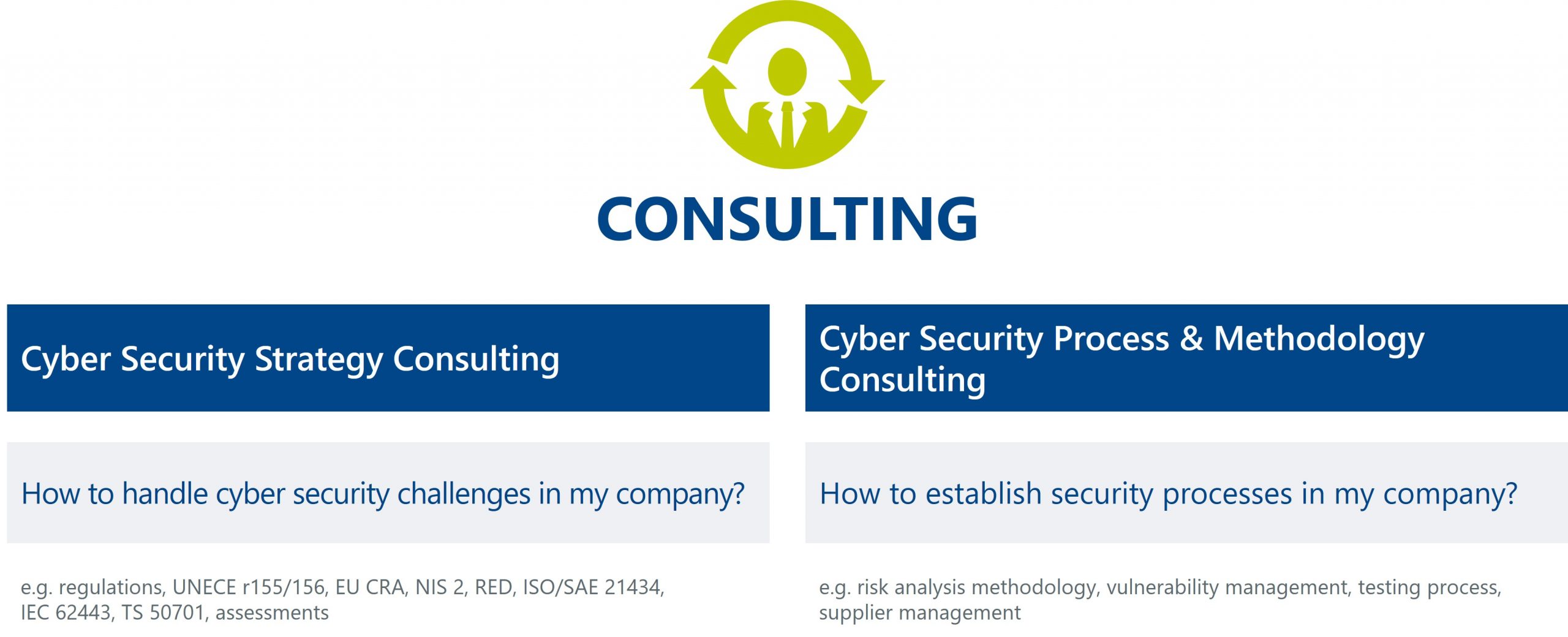
Learn more about our cyber security consulting services.
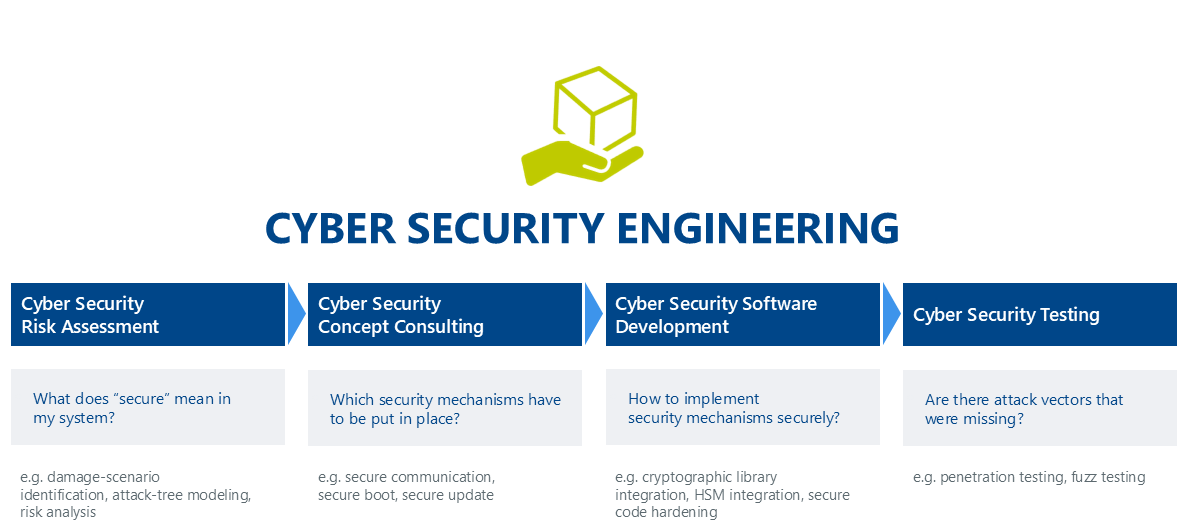
Learn more about our cyber security engineering services.
Manufacturing is going digital. Increasingly connected factories and processes are prime targets for cyber attacks. Learn more about how we help operators and vendors protect their production lines against cyber attacks.