Sebastian Schrimpf
Industrial Solutions
Productivity rises when machines and systems go digital and get connected. So does the likelihood of cyber attacks. No wonder, then, that new products have to satisfy ever more stringent cyber security requirements. Long-term business success hinges on companies’ ability to guard against cyber threats. This is not just about complying with new regulations such as the EU Cyber Resilience Act (CRA), EU NIS 2 and the Delegated Act of the Radio Equipment Directive (RED); it is also about protecting the resilience of your and your customers’ networks. Let us accompany you on this journey. Opt for a pragmatic security solution that suits your needs and is tailored to match your risks.
Espionage, sabotage, extortion, and even physical damage – cyber crime comes in many guises. Attacks can shut down entire production lines or render digital products unusable on a wide scale – with serious financial consequences and reputational damage. Many industrial companies have recognized the risks posed by cyber threats, but believe themselves in a false sense of security, as the cyber security experts at the Aachen-based Fraunhofer Institute for Production Technology IPT show.
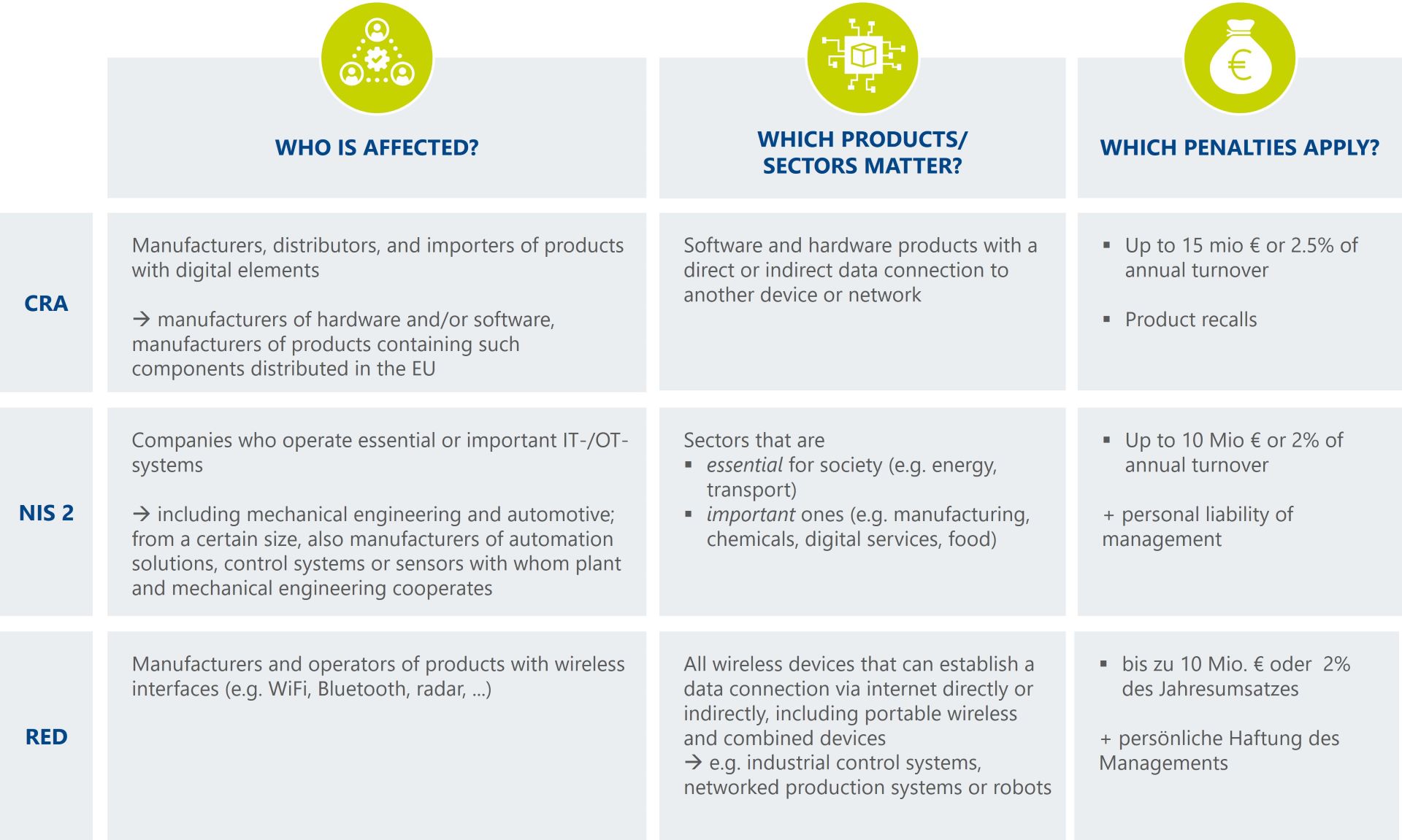
The EU updated its regulations and issued new directives to keep the mounting threat at bay and minimize risk. Three directives are particularly relevant for operators and manufacturers in the industrial sector: NIS 2 is to be transposed into national law as early as October of 2024. The Radio Equipment Directive (RED) is already in force. However, the RED Delegated Act has adopted new requirements that will become mandatory from August 2025. The Cyber Resilience Act (CRA) passed in October 2024 will become binding from 2027.
We consider your individual requirements, technical constraints and legacy processes – from cyber security strategy consulting, process and methodology consulting to cyber security risk assessment, concepts, software development and testing. Of course, we always take current regulations such as UNECE r155/156, EU CRA, NIS2, RED, ISO/SAE 21434, IEC 62443, TS 50701 into account.
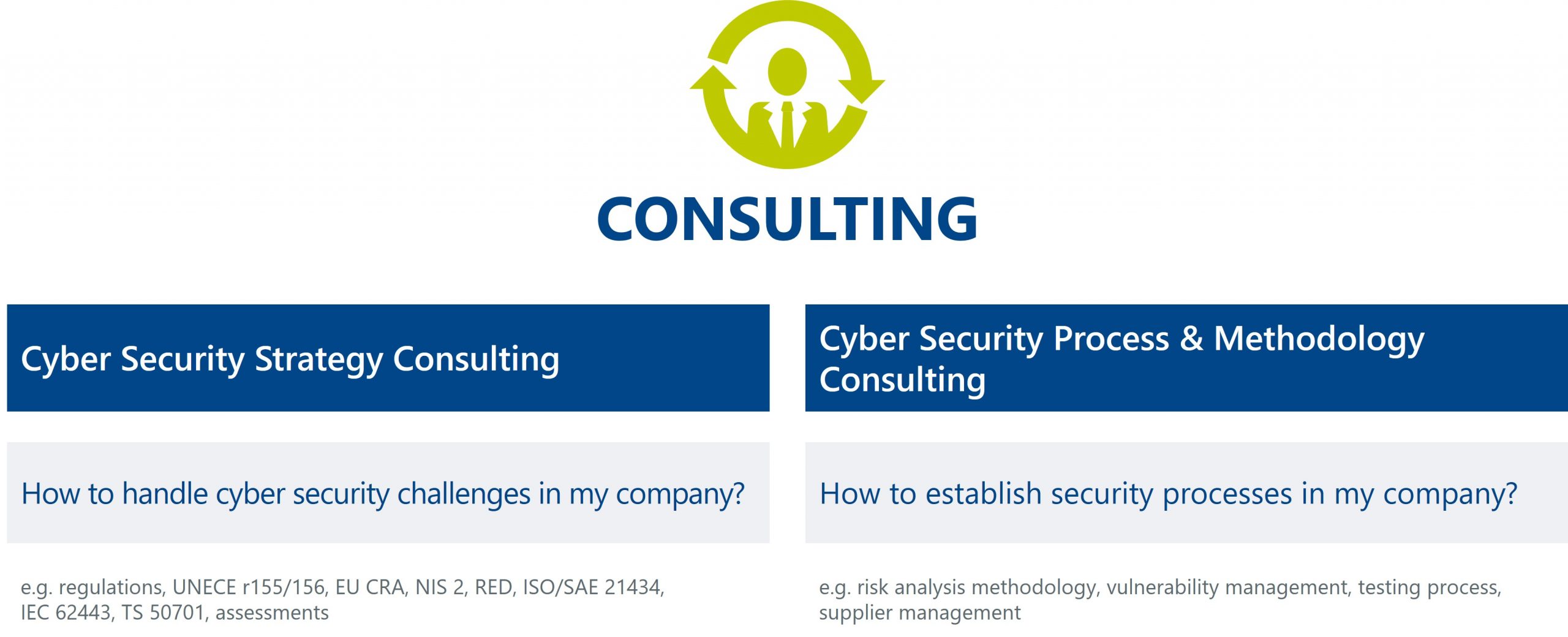
Our consulting services empower you to proactively identify and mitigate security risks. Together, we craft a tailored security strategy that holistically safeguards your IT/OT infrastructure. From risk analysis and vulnerability management to supplier management – we support you every step of the way. With our hands-on approach, we implement a comprehensive security concept that boosts your resilience against cyber threats and attacks.
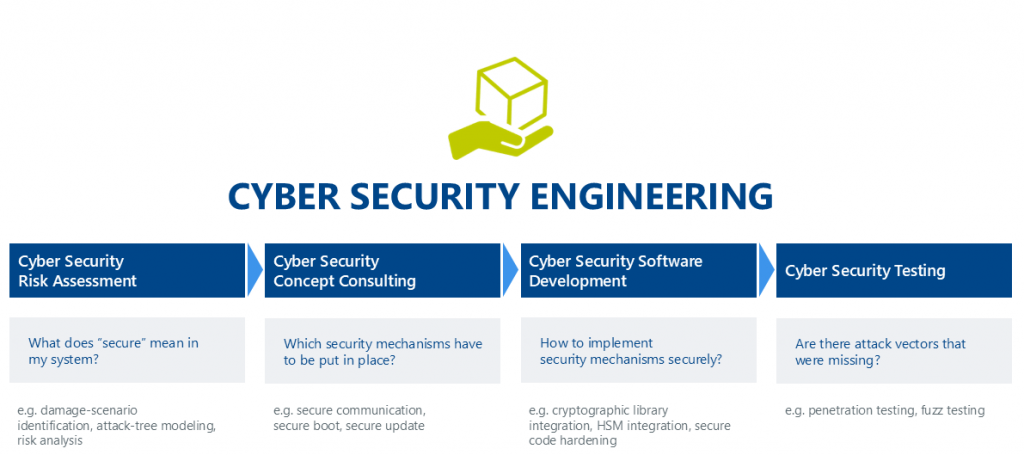
Our comprehensive cyber security engineering services help you implement robust security measures practically and efficiently. We start with a thorough risk assessment – identifying potential damage scenarios, modeling attack paths, and systematically uncovering vulnerabilities through detailed analyses. Based on these insights, we create a tailored security concept that outlines the necessary protective mechanisms. We then implement these requirements technically, building a reliable and resilient software foundation. To ensure long-term security, we continuously verify the effectiveness of these measures with cyber security tests.